Creating NAT Rules
To create a NAT rule, navigate to the Edge Gateway, right-click and select “Edge Gateway Services”. Then select the NAT tab.
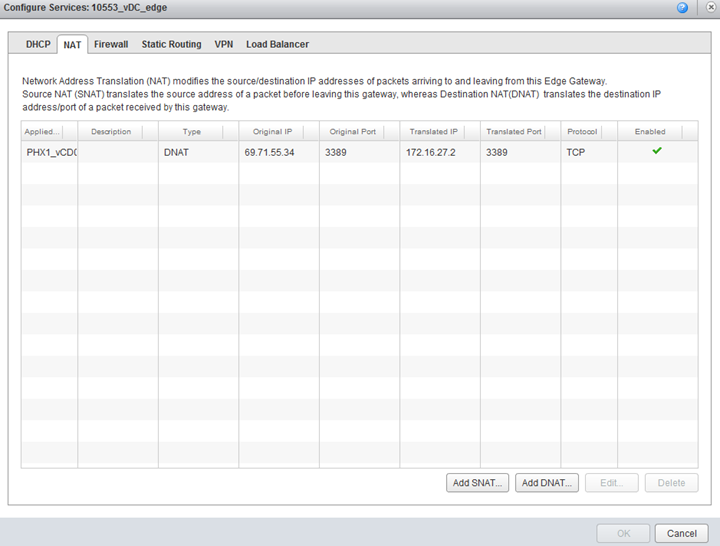
The “Add SNAT” button will start the Source Nat dialog, and the “Add DNAT” button will start the Destination Nat dialog. SNAT rules translate the source IP of outbound packets, and DNAT rules translate the destination of inbound packets. At least one of each rule is required in order for traffic to flow across the Edge Gateway into the vDC. Some common examples of necessary NAT rules can be found below. Note that for any external communication, NAT rules should be applied to the External network (the one containing “EXT” in the name).
SNAT Rule Example: Many-To-One Outbound
This rule translates the source IPs for all VMs in the vDC to the external IP of the Edge Gateway.
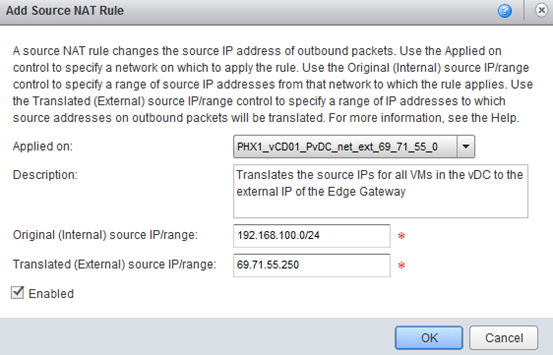
Any packet from the subnet 192.168.100.0/24, which is the internal Org VDC network for this vDC, is translated to come from the external IP. Note that this type of rule is required for a VM to reach the internet.
DNAT Rule Example: One-To-One Inbound
This rule translates all of the inbound packets for an external IP to go to a specific internal IP.
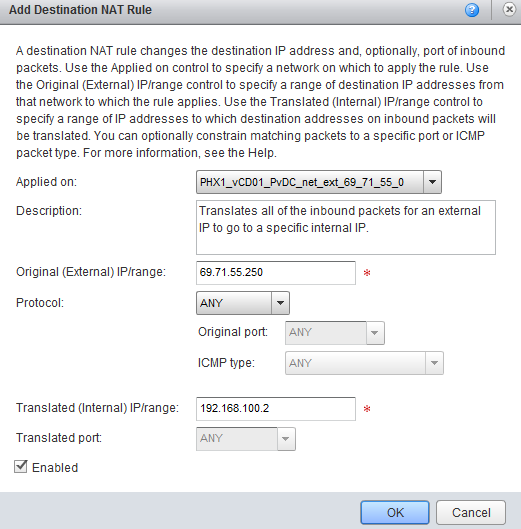
This method consumes an entire external IP, and should only be used if a front-facing web server or other application server is hosted in that vDC.
DNAT Rule Example: One-To-One Inbound (Port NAT)
This rule translates the destination IPs for a specific port on the external IP of the Edge Gateway to a specific internal IP of a VM in the vDC.
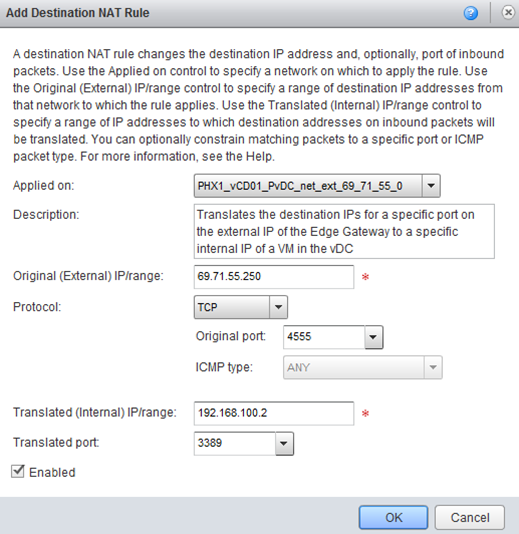
This rule specifically directs the outside port to port 3389 on the internal IP, which allows RDP access.
No matter how traffic is routed the NAT rules must be created, along with corresponding Firewall rules. See Firewall Rule Management for more information on configuring Firewall rules. Note that this type of rule is necessary to allow traffic to reach a VM.
