Before looking at Network Management in vCloud, it may be beneficial to look at the different types of network appliances available in Green Cloud IaaS and how your network architecture will differ with each of them.
Types of Network Appliances
GreenCloud IaaS environments can be deployed with various types of networking appliances, including:
- an Edge Gateway router,
- a Cisco ASAv firewall, or
- a third-party bring-your-own-device (BYOD) installation.
An Edge Gateway is a virtual router embedded in vCloud, whereas a Cisco ASAv is a different virtual router which is created outside of vCloud and imported. BYOD network appliances can be created or imported. Each type of virtual router manages external-facing connections, as well as internally-defined subnets and networks. The practical differences as they pertain to Org VDC networks are as follows:
- Edge Gateways use the vCloud interface to directly change network interfaces and NAT/Firewall rules
- Cisco ASAv’s and BYOD’s use direct SSH login or GUI management to change those components
- Edge Gateways use Routed networks to directly interface with external networks
- Cisco ASAv’s and BYOD’s use Isolated networks to connect to VLAN-backed external networks
For further information, see the Edge Gateway and Cisco ASAv index articles.
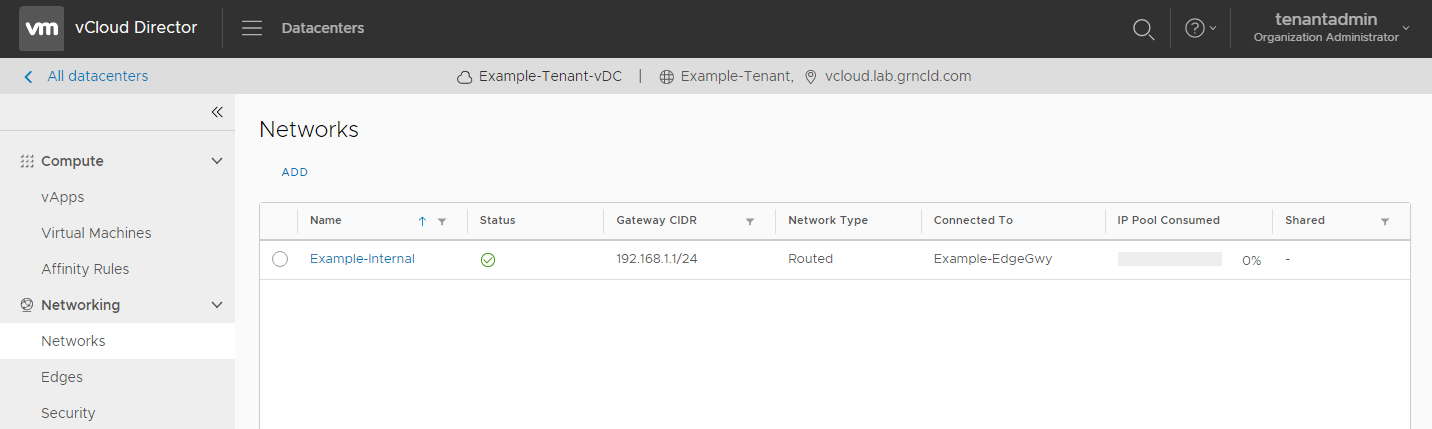
View Org VDC Networks
To view the Org VDC networks on a VDC, log in to vCloud, select the Data Centers tab, double-click to enter a vDC, and select the Networks tab.
Types of Org VDC Networks
There are two types of Org VDC networks in vCloud:
- Isolated networks are for private IP subnets.
- These networks can be used to allow vApps to communicate with one another, and can be used to create IP pools on which VMs can be addressed.
- These can be used to allow internal communication to the external internet through a Cisco ASAv. For more information on Cisco ASAvs, please see the Cisco ASAv Reference Guide.
- Routed networks are connected directly to an Edge Gateway.
- They can be used to allow internal communication to the external internet, and are otherwise identical to Isolated Networks.
- These can be used in place of isolated networks when an Edge Gateway is present in the vDC. For more information on Edge Gateways, please see the Edge Gateway KB section.
Network Creation
To create a new Network, click the blue “Add” in the Networks view as shown above. In the dialog, select the type of network to be created.
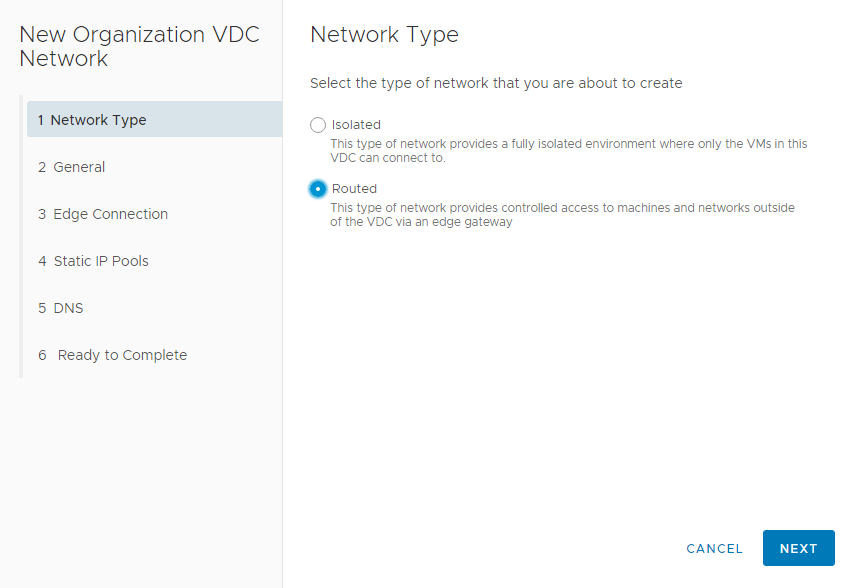
If an Edge Gateway is present, create a routed network , otherwise a new isolated network can be created.
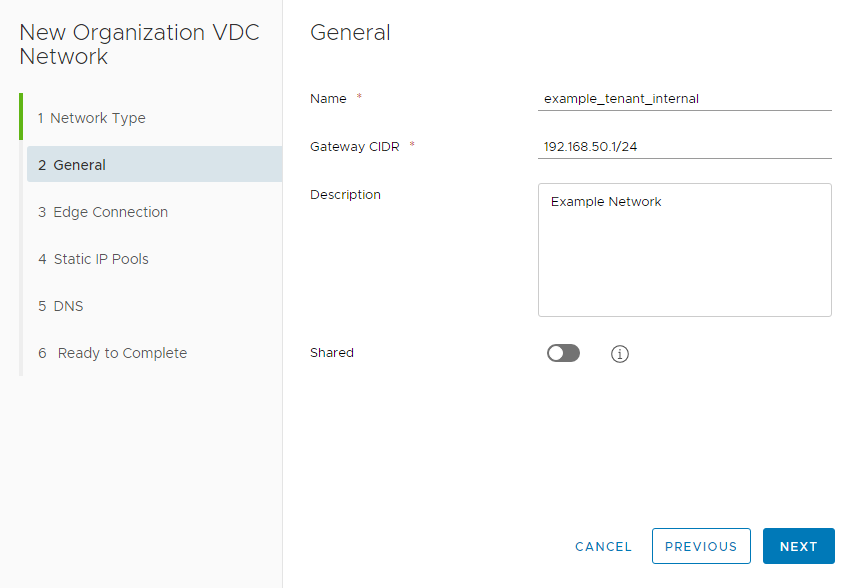
At the next page, enter the network’s display name and Gateway address in CIDR format. In this example we use 192.168.50.1 as our Gateway.
If you are creating a Routed network, you will see an Edge Connection screen next. Select the relevant Edge Gateway and which type of Interface you wish to use, then select Next.
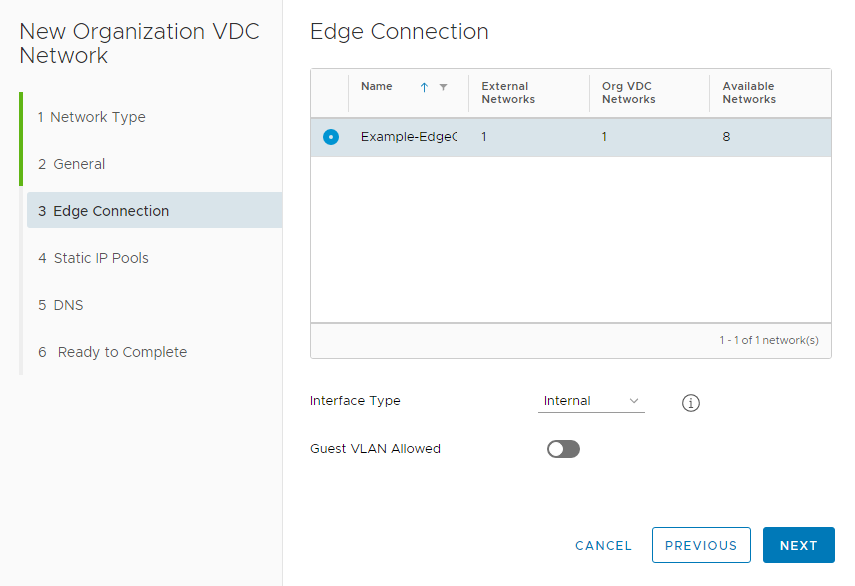
There are two types of Interfaces through which a Routed Network can connect to an Edge Gateway: Internal or Distributed.
- Use ‘internal interface’ when you want to connect to one of the edge gateway’s internal interfaces
- Use ‘distributed’ when you want fast and efficient East-West routing. The network will be connected to an internal interface of a distributed router that is exclusively associated with this gateway
At the next screen, allocate internal IP pools for the subnet. Enter a range in the box and select “Add”. The example below includes a subnet on 192.168.50.0/24, with a Gateway on 192.168.50.1 as defined above, and allocates 192.168.50.2-192.168.5.100.
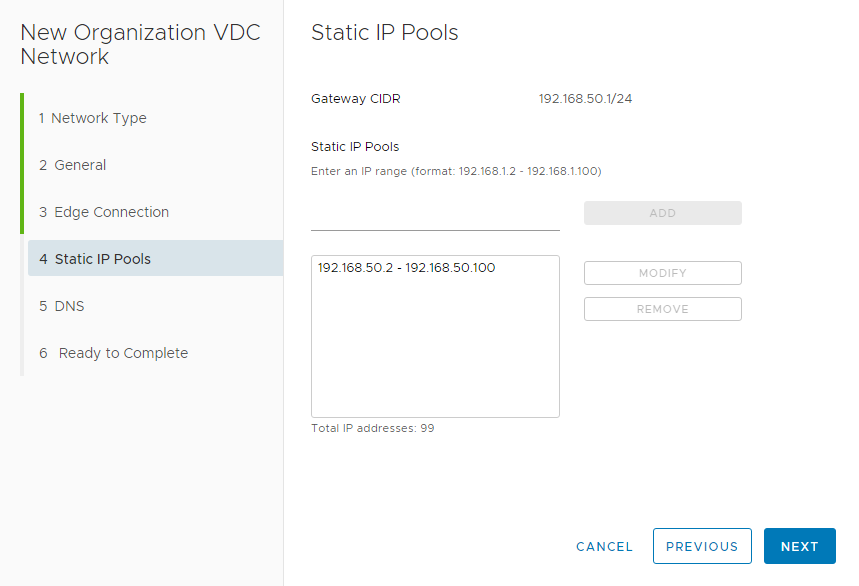
Select “Next” when the IP configuration is correct. You have the option of defining DNS servers at the penultimate screen but this step is not mandatory. At the final screen, verify that all information is correct, then click “Finish”.
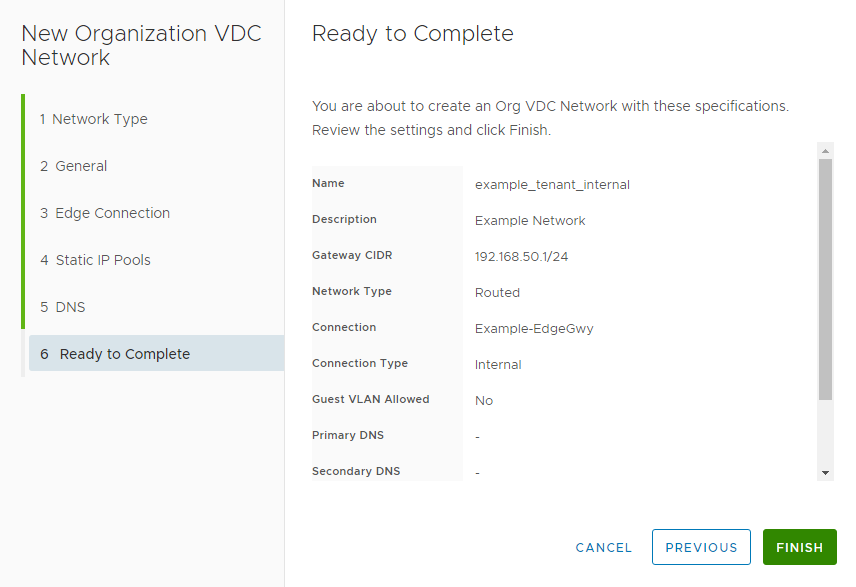
At this point the Network is complete. If you reach the network quota for a vDC you will not be able to create any more networks. The network quota can be increased by contacting GreenCloud support.
Connecting a VM to a Network
In order to reach the internet, each VM must be connected to an Org VDC network with internet access. This will be either a Routed network with access to an Edge Gateway, or an Isolated network with access to an ASAv. To connect a VM to a Network, first go to that VM’s vApp. Select “Actions” to find the “Add Network” option.
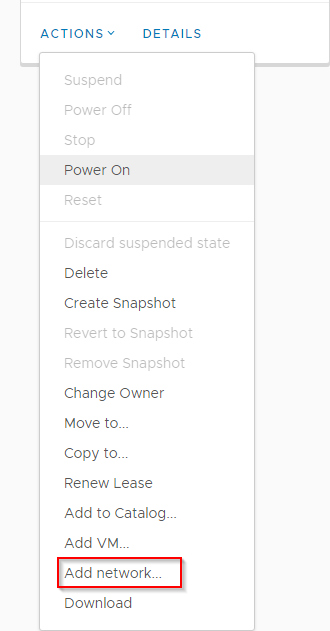
Select the “Org VDC Network” option, then select the relevant network that VM should land on.
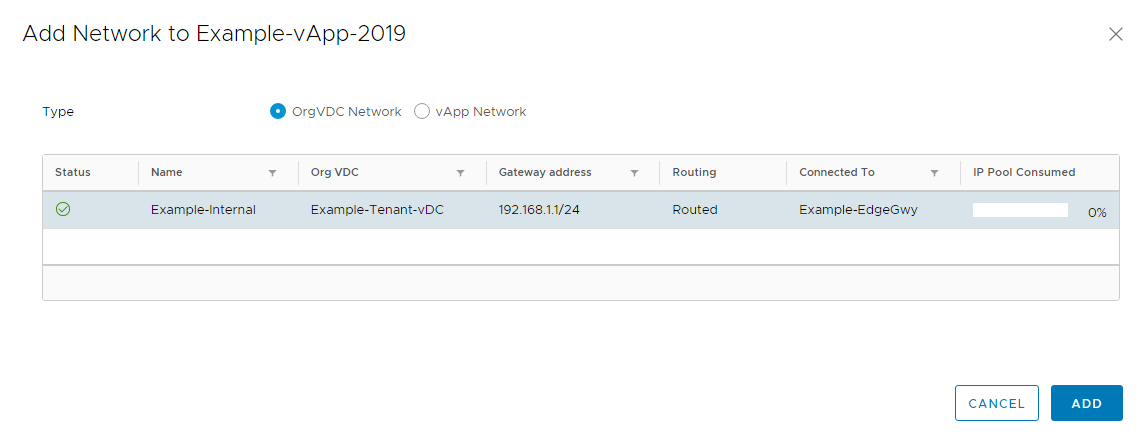
Once this Network has been added to the vApp, go to the “Virtual Machines” section from the left-hand navigation bar. Select “Details” for the relevant VM, then go to the NICs subsection of the Hardware section.

Under “Network”, select the Network that you added to the vApp, then make sure the IP mode is correct for that Network. In this example, we are allowing the Network to automatically assign a Static IP to the VM from an IP pool.
The VM will now have connectivity to that Org VDC network, and will have the ability to use IPs from that network. If the Org VDC network is routed to an Edge Gateway or connected to a Cisco ASAv, the VM should be able to communicate with the internet. Please note that the proper NAT and Firewall rules will need to be configured in order to allow communication.
