NAT enables private IP networks defined by RFC 1918 to connect to the Internet. NAT translates the private IP of a host into routable addresses that can be used on the Internet. This allows a single public IP to be used for multiple private hosts. There are two types of NAT available on the ASAv: Object NAT, and Twice NAT. Twice NAT is the preferred method of creating NAT rules. Below are the steps to create a NAT rule on your ASA using Static Twice NAT. Be sure to create the network and service objects prior to creating the NAT rule.
1. Navigate to NAT Rules
Select Configuration in the upper left, then Firewall in the lower left. Select the NAT Rules section from the left-hand bar.
2. Add NAT Rule
Select Add from the NAT Rules window, and complete the configuration in the NAT Rule Creation window. See below for field descriptions and definitions.
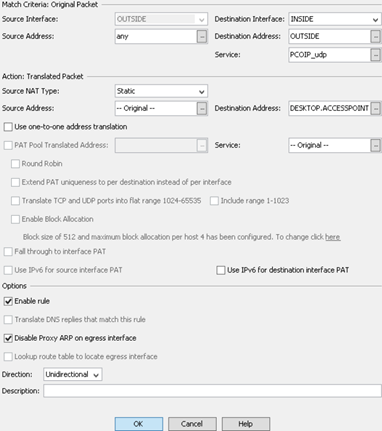
- Original Packet: This section defines the criteria the original packet must meet to be passed.
- Source Interface: This is the OUTSIDE interface. The interface to which the original packet is arriving should always be the external interface.
- Source Address: In most cases this will be ‘any’. This means you can specify the source address.
- Destination Interface: In most cases this will be INSIDE. This is the Interface on which the destination object is addressed.
- Destination Address: This is the translated address of the destination object. This can be set to an interface or object. In most cases it will be the OUTSIDE interface. To use a secondary public IP as the destination address, you must first create a network object for that IP address.
- Service: This is the destination service, or port. In most cases this is the same as the destination port. However, in the case of port translation, this is where you would define the translated port. For example, if RDP (normally 3389) should be translated to 43389, first a service object must be for 43389. Then that service object would be applied here to the original packet service.
- Action: Translated Packet
- Source NAT Type: In most cases this will be Static.
- Soruce Address: In most cases this will be Original.
- Destination Address: This is the network object of the destination on the protected network.
- Service: In most cases this will be Original. Using the RDP high port example, first a service object for RDP 3389 would need to be created, and then applied to the Service of the translated packet.
- In most cases the remaining check boxes are not used.
- Options
- The rule must be enabled for it to be used.
- Be sure to ‘Disable Proxy ARP on egress interface’
- Set the direction to unidirectional. This prevents the destination address from initiating connections to the real address.
3. Verify NAT Rule Order
When using Twice NAT, the rule order matters. By default, when adding a rule it will be the last rule listed prior to any Object NAT rules you may have. If necessary, you can re-order the Twice NAT statements using the up/down arrows just above the NAT rules.